Of Corporate Data Is Now Stored On The Cloud
To higher defend each their companies and their users, firm leaders must familiarize themselves with the darknet and its threats and opportunities. When corporations are hacked and their knowledge is stolen, that knowledge usually appears on the market on the so-referred to as darknet. Earlier this year, for example, consumer data from each themega-hack of Yahoo and the uTorrent breach showed up on the darknet’s illicit marketplaces. As InformationWeek recently put it, the darknet is “where your stolen identification goes to live.” Think of it as mass e-commerce for the black market (right here’s a good primer). A pc community with restricted entry that’s used mainly for illegal peer-to-peer file sharing.
“Darknet” was coined within the Nineteen Seventies to designate networks isolated from ARPANET (the government-founded army/academical network which developed into the Internet), for safety functions. Darknet addresses could obtain knowledge from ARPANET however didn’t appear in the network lists and would not reply pings or other inquiries. The term “darknet” is usually used interchangeably with the “darkish net” due to the quantity of hidden providers on Tor’s darknet. The term is commonly inaccurately used interchangeably with the deep internet as a result of Tor’s historical past as a platform that could not be search-indexed.
Everything evil proliferates within the mostly inaccessible outer reaches of the web. Researchers at Bat Blue Networks today released a report outlining the primary actors and actions on the Darknet — a subset of the Internet the place the websites are unindexed and accessible only via the onion router community. This paper described “darknet” extra usually as any type of parallel network that is encrypted or requires a selected protocol to permit a user to hook up with it.
Any address or data requested utilizing the browser is transmitted via the Tor network. The Tor network is a safe, encrypted protocol to make sure privateness of data and communications on the internet.
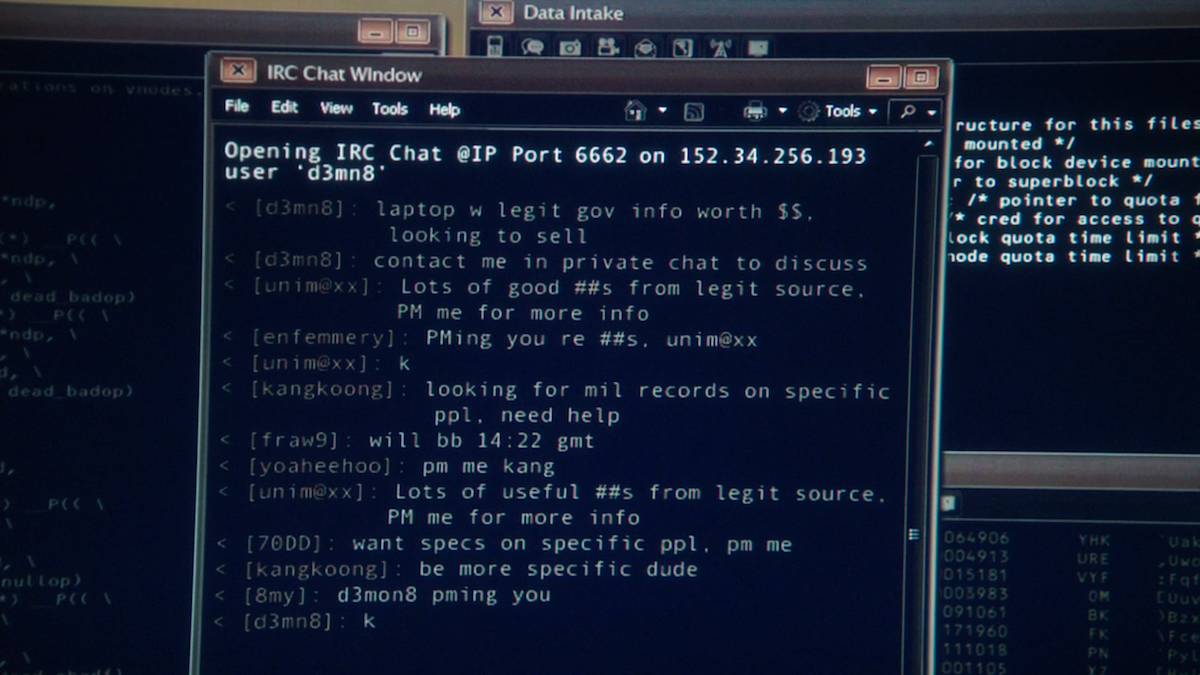
- It is difficult to track users within the darknet and so it grew to become a haven free of charge speech and expression, especially in international locations the place the internet is heavily policed and blocked.
- For instance, academic databases are only out there to faculty and college students, and corporate networks are solely out there to workers.
- Peer-to-peer networks and self-hosted web sites are additionally a part of the darknet.
- Sites here aren’t listed by search engines like google and yahoo because they are merely not accessible to them.
Free Vpn For Android
Data anonymization platforms are assembly these calls for within the forms of darkish wallets and underground networks. Tor is certainly one of such underground networks that was carried out for the purpose of protecting customers’ identities. For users who discover Tor too complicated or need larger performance, a reliable официальный адрес магазин гидры на тор VPN like ProtonVPN is a good alternative. A VPN will encrypt your online site visitors and forestall attackers from monitoring your shopping activity. Once you put in the VPN app, all it takes is a single click on to establish an encrypted VPN connection.
When utilizing a VPN, more than likely solely you and your VPN provider will know what websites you’ve visited. If you’re careful, you possibly can safely entry and browse the dark net. First, download the Tor browser, which provides you with entry to dark web pages and hold you anonymous while searching the typically-seedier corners of the web. If that name sounds sinister, it’s because the dark internet encourages activity that individuals would quite hide from view. The dark web is where people can buy unlawful drugs and firearms.
“Tor” servers — derived from “The Onion Router” — are undetectable from search engines and offer customers complete anonymity whereas surfing the net. At the identical time, darkish internet web site publishers are also nameless due to particular encryptions provided by the protocol. To this impact, consumers are more and more choosing products that profess knowledge privacy and cybersecurity. Users that have interaction in digital marketplaces, digital funds, and community forums are demanding more anonymity in the best way their online communications and transactions are shared.



